GTU MCWC (3170710) S-2024 Paper Solution
Q.1(a) Define IMSI,MSRN and MSISDN.(3 Marks)
IMSI (International Mobile Subscriber Identity):
Definition: A 15-digit unique code identifying a mobile subscriber in a network.
Use: Authentication and tracking within cellular networks.
IMEI (International Mobile Equipment Identity):
Definition: A unique 15-digit number assigned to every mobile device.
Use: Identifies the handset and blocks stolen devices.
MS-ISDN (Mobile Station International Subscriber Directory Number):
Definition: The actual phone number linked to a SIM card.
Use: Routing calls and messages to the intended subscriber.
Q.1(b) Differentiate Circuit Switching and Packet Switching. (4 Marks)
| Aspect | Circuit Switching | Packet Switching |
|---|---|---|
| Definition | Establishes a dedicated path for communication. | Data is divided into packets sent independently. |
| Connection Type | Connection-oriented. | Connectionless. |
| Data Transmission | Continuous stream. | In packets with reassembly at the destination. |
| Bandwidth Usage | Fixed for each session. | Shared among multiple users. |
| Delay | Minimal once the connection is established. | Delays due to routing and reassembly. |
| Example | Telephone calls (PSTN). | Internet, email, and video streaming. |
Q.1(c) Define Channel Capacity. Describe Nyquist and Shannon criteria to find Channel Capacity. (7 Marks)
Definition:
Channel capacity is the maximum rate at which data can be transmitted over a communication channel without significant errors.
Features:
Determines efficiency of communication systems.
Depends on bandwidth, signal strength, and noise.
Guides the design of telecommunication systems.
Shannon Formula:
C = B ⋅ log2(1 + SNR)
Where:
C: Channel capacity (bits per second).
B: Bandwidth (Hz).
SNR: Signal-to-Noise Ratio.
Nyquist Formula:
C = 2B ⋅ log2(M)
Where:
M: Number of distinct signal levels.
B: Bandwidth (Hz).
Key Factors Affecting Capacity:
Bandwidth: Higher bandwidth increases capacity.
Signal-to-Noise Ratio (SNR): Improved SNR enhances data rate.
Encoding Techniques: Better encoding allows efficient data transmission.
Interference: Reduces channel efficiency.
Uses:
Determines network performance.
Helps in wireless communication planning.
Optimizes data rates in digital systems.
Q.2(a) Compare TDM and FDM. (3 Marks)
| Feature | TDM (Time Division Multiplexing) | FDM (Frequency Division Multiplexing) |
|---|---|---|
| Method | Allocates different time slots for each signal. | Allocates different frequency bands for each signal. |
| Bandwidth Usage | Efficient when the number of signals is small. | Suitable for a large number of signals with varying bandwidth. |
| Signal Separation | Based on time, each signal uses the same frequency channel. | Based on frequency, each signal has a distinct frequency band. |
| Applications | Used in digital transmission systems, telephony, and networking. | Used in analog radio, TV broadcasting, and satellite communication. |
Q.2(b) Describe different types of Antennas. (4 Marks)
1. Dipole Antenna:
A simple antenna that consists of two metal rods.
Commonly used for radio and television transmissions.
2. Monopole Antenna:
A type of dipole antenna with one-half of the antenna grounded.
Used in mobile communication systems.
3. Parabolic Antenna:
A high-gain antenna shaped like a parabola.
Used in satellite communication for receiving and transmitting signals.
4. Yagi-Uda Antenna:
A directional antenna with multiple elements: one dipole (driven element) and several parasitic elements.
Commonly used in TV reception and amateur radio.
5. Horn Antenna:
A flared antenna that directs radio waves in a specific direction.
Used in radar systems and microwave testing.
Q.2(c) Draw and Describe GSM Architecture. (7 Marks)
Definition:
The GSM (Global System for Mobile Communications) is a digital mobile communication system widely used worldwide. It is designed to standardize cellular communication.
Features:
Provides voice and data services.
Supports international roaming.
High security using encryption and SIM authentication.
Divides areas into cells for efficient network coverage.
Uses:
Enables mobile calls and SMS.
Supports internet access through GPRS/EDGE.
Facilitates secure and reliable mobile communication.
Components and Their Roles:
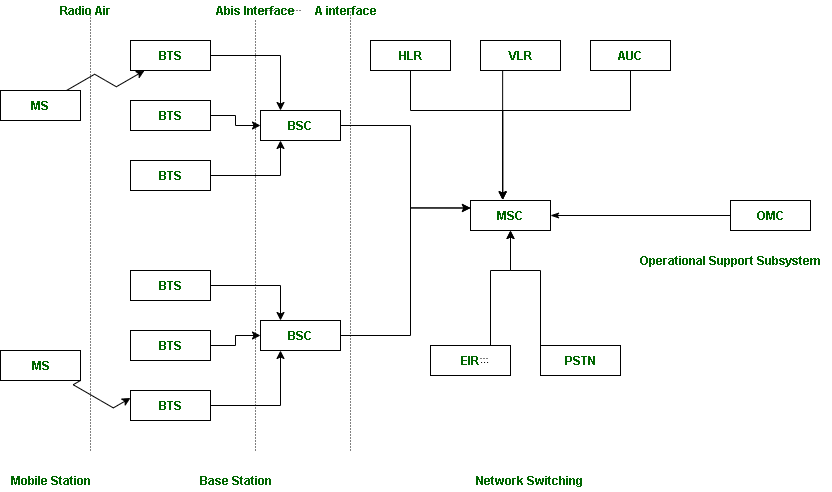 Source: geeksforgeeks
Source: geeksforgeeks
Mobile Station (MS):
User equipment like mobile phones.
Connects users to the network.
Mobile Station (MS) = Mobile Equipment(ME) + Subscriber Identity Module (SIM)
Now, these mobile stations are connected to tower and that tower connected with BTS through TRX.
Base Station Subsystem (BSS):BSS handles traffic and signaling between a mobile phone and the network switching subsystem.
Base Transceiver Station (BTS): Handles wireless communication with devices.
Base Station Controller (BSC): Manages BTS and allocates resources.
Network and Switching Subsystem (NSS):That carried out call and mobility management functions for mobile phone present in network.
Mobile Switching Center (MSC): Core component for call routing and switching.
Visitor Location Register (VLR): VLR is a database which contains the exact location of all mobile subscribers currently present in the service area of MSC.
Home Location Register (HLR):HLR is a database containing pertinent data regarding subscribers authorized to use a GSM network.
AUC : AUC stands for Authentication Center. AUC authenticates the mobile subscriber that wants to connect in the network.
EIR : EIR stands for Equipment Identity Register. EIR is a database that keeps the record of all allowed or banned in the network. If you are banned in the network then you can’t enter the network, and you can’t make the calls.
Operation and Support Subsystem (OSS):
Manages and monitors network operations.
Q.2 OR (c) Explain Mobile IP. (7 Marks)
Definition:
Mobile IP (Internet Protocol) is a communication protocol designed to enable mobile devices to move between networks while maintaining a permanent IP address.
Features:
Provides seamless connectivity for mobile users.
Supports both IPv4 and IPv6.
Works by using home and foreign agents for packet delivery.
Components:
Mobile Node (MN): A device that moves between networks, like a smartphone or laptop.
Home Agent (HA): A router in the home network that tracks the MN's location and forwards packets.
Foreign Agent (FA): A router in the visited network that provides temporary care-of address (CoA) to the MN.
Correspondent Node (CN): A device communicating with the MN.
 source:geeksforgeeks
Working of Mobile IP:
source:geeksforgeeks
Working of Mobile IP:
When the MN moves to a foreign network, it registers with the FA and obtains a CoA.
The HA tunnels packets to the CoA using encapsulation.
The FA decapsulates packets and delivers them to the MN.
Outgoing packets are sent directly from the MN to the CN.
Advantages:
Ensures uninterrupted service during mobility.
Supports real-time applications like VoIP.
Limitations:
Overhead due to encapsulation and tunneling.
Potential delays in handover between networks.
Applications:
Enables mobile internet access for devices in motion.
Used in IoT devices requiring constant connectivity.
Q.3(a) Describe Multi-path Propagation and Fading. (3 Marks)
Definition:
Multi-path propagation occurs when transmitted signals reach the receiver via multiple paths due to reflections, diffractions, or scattering. This can cause the signal to interfere with itself.
Fading:
Fading refers to the variation in signal strength over time due to interference and multipath propagation. The two main types of fading are:
Fast Fading: Occurs over short periods or distances, typically caused by small obstacles.
Slow Fading: Occurs over longer periods or distances, usually due to large obstacles or changes in the environment.
Impact of Multi-path Propagation and Fading:
Leads to signal degradation, interference, and potential loss of communication.
Affects wireless communication systems like mobile networks, GPS, and Wi-Fi.
Q.3(b) Compare HLR and VLR. (4 Marks)
| Feature | HLR (Home Location Register) | VLR (Visitor Location Register) |
|---|---|---|
| Location | Central database in the mobile network, stores permanent subscriber information. | Temporary database located in the visited network. |
| Stored Information | Stores subscriber’s profile, service information, and current location. | Stores information of subscribers currently in the area. |
| Usage | Used for call routing, authentication, and managing user profiles. | Provides temporary data and facilitates call routing for roaming users. |
| Functionality | Performs updates to subscriber data and handles requests for authentication and service activation. | Caches information from HLR and manages real-time data for active roaming subscribers. |
Q.3(c) Describe Spread Spectrum Technology. (7 Marks)
Definition:
Spread Spectrum Technology (SST) is a method of transmitting radio signals by spreading the signal over a wide bandwidth. This reduces interference and improves signal security.
Types of Spread Spectrum:
Frequency Hopping Spread Spectrum (FHSS):
The carrier frequency hops to a different frequency at regular intervals.
Example: Bluetooth communication.
Direct Sequence Spread Spectrum (DSSS):
The signal is multiplied by a pseudo-random noise sequence (spreading code), making it appear over a wider frequency spectrum.
Example: Wi-Fi (802.11b/g).
Chirp Spread Spectrum (CSS):
The frequency of the signal continuously increases or decreases over time.
Example: LoRaWAN.
Advantages of Spread Spectrum Technology:
Resistance to Interference:
Spread spectrum signals are more resistant to interference, as the signal occupies a wide bandwidth.
Security:
The use of a pseudo-random sequence makes it difficult to intercept the signal.
Multipath Resistance:
Since the signal is spread over a wide range of frequencies, it can counteract the effects of multipath interference.
Coexistence with Other Signals:
Multiple spread spectrum systems can operate in the same frequency range without causing interference.
Applications:
Military Communications: For secure, interference-resistant communication.
Wireless Networks: Wi-Fi and Bluetooth utilize DSSS and FHSS, respectively.
GPS: Uses spread spectrum to improve location accuracy and prevent jamming.
Q.3(a) Describe billing and charging in GPRS. (3 Marks)
Definition:
Billing and charging in GPRS (General Packet Radio Service) refer to the process of calculating and collecting charges for the data services provided to users.
Billing Process:
Packet-Based Billing:
GPRS uses packet-switching, meaning users are billed for the amount of data transmitted rather than the time spent connected.
Charging Parameters:
Volume-Based Charging: Based on the amount of data (in kilobytes or megabytes) used.
Time-Based Charging: Billing for the duration the user is connected to the network, applicable for certain services.
Usage Accounting:
GPRS networks monitor and track user activity, including data volume, session times, and service types to generate bills.
Components Involved:
Gateway GPRS Support Node (GGSN):
Interacts with external networks and provides data routing, accounting, and billing services.
Charging Gateway Function (CGF):
Collects and processes usage data to produce billing records.
Q.3 OR (b) Describe Propagation Modes in Wireless Communication. (4 Marks)
1. Line-of-Sight Propagation:
.png)
source:geeksforgeeks
The signal travels directly between the transmitter and receiver without obstructions.
Used in microwave communication and satellite systems.
2. Ground Wave Propagation:
.png)
source:geeksforgeeks
The signal follows the Earth's surface, typically used for AM radio waves.
It is effective over short to medium distances.
3. Skywave Propagation:
.png)
source:geeksforgeeks
The signal is reflected from the ionosphere back to Earth.
Used for long-range communications, such as shortwave radio.
4. Tropospheric Propagation:
.png)
source:geeksforgeeks
Occurs in the lower atmosphere, where the signal bends due to temperature and humidity variations.
Used in long-range terrestrial communications like TV and radio broadcasting.
Q.3 OR (c) Describe Frequency Hopping Spectrum Technology. (7 Marks)
Definition:
Frequency Hopping Spread Spectrum (FHSS) is a method of spread spectrum communication where the transmission frequency of the signal is changed at regular intervals according to a predetermined sequence.
 source:geeksforgeeks
source:geeksforgeeks
How FHSS Works:
The sender and receiver both know the frequency hopping sequence.
The sender transmits data over one frequency, and after a set period (hop), it switches to another frequency.
This hopping pattern continues throughout the transmission.
Advantages of FHSS:
Reduced Interference: Since the signal rapidly hops between frequencies, it avoids interference from other devices on a specific frequency.
Increased Security: The unpredictability of the hopping sequence makes it difficult to intercept the communication.
Resistance to Jamming: If the transmission is jammed on one frequency, the system continues to operate on other frequencies in the sequence.
Applications:
Bluetooth: Uses FHSS to enable communication between devices in close proximity.
Military Communication: Provides secure, interference-resistant communication for tactical operations.
Q.4(a) Write Architectural Difference in GSM and GPRS. (3 Marks)
| Feature | GSM | GPRS |
|---|---|---|
| Definition | Global System for Mobile Communication. | General Packet Radio Service. |
| Data Type | Circuit-switched for voice. | Packet-switched for data. |
| Speed | 9.6 kbps. | Up to 171.2 kbps. |
| Applications | Voice calls, SMS. | Internet access, MMS, email. |
| Connectivity | Always on for voice. | Always on for data. |
Q.4(b) Enlist various Multiple Access Technologies and Describe CDMA. (4 Marks)
Enlisted Technologies:
FDMA (Frequency Division Multiple Access): Divides frequency bands among users.
TDMA (Time Division Multiple Access): Allocates time slots to users.
CDMA (Code Division Multiple Access): Uses unique codes for each user to share the same frequency.
OFDMA (Orthogonal Frequency Division Multiple Access): Uses sub-carriers within a frequency band.
Description of CDMA:
Code Division Multiple Access (CDMA) allows multiple users to share the same frequency band by assigning a unique code to each user. The receiver decodes the signal using the same unique code, making the communication secure and efficient.
Features:
High capacity and scalability.
Resists interference and provides secure communication.
Example:
Used in 3G networks for mobile communication.
Q.4(c) Describe Automatic Repeat Request (ARQ). (7 Marks)
Definition:
Automatic Repeat Request (ARQ) is an error-control protocol used in data communication to ensure reliable transmission by detecting errors and retransmitting corrupted data.
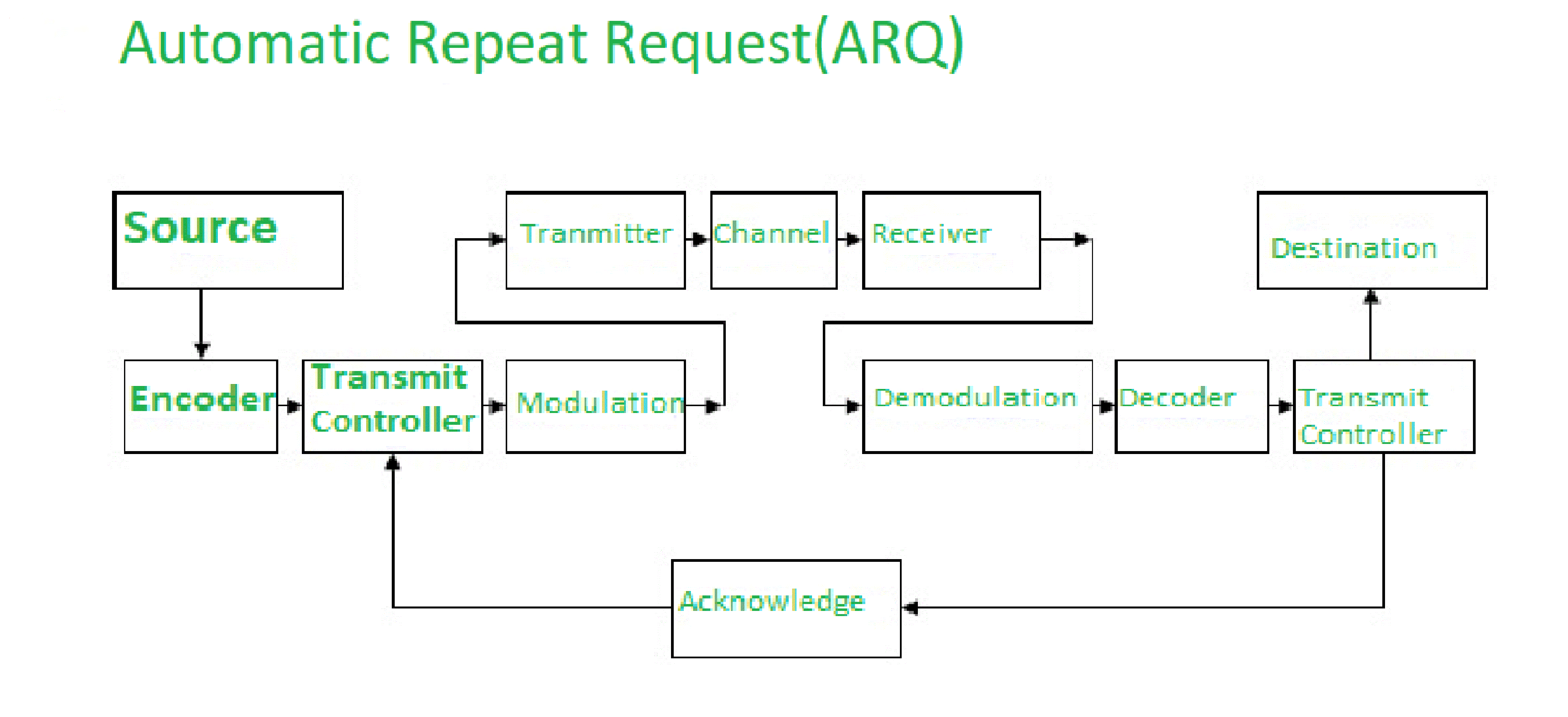
source:geeksforgeek
Types of ARQ:
Stop-and-Wait ARQ:
The sender transmits one frame at a time and waits for an acknowledgment before sending the next frame.
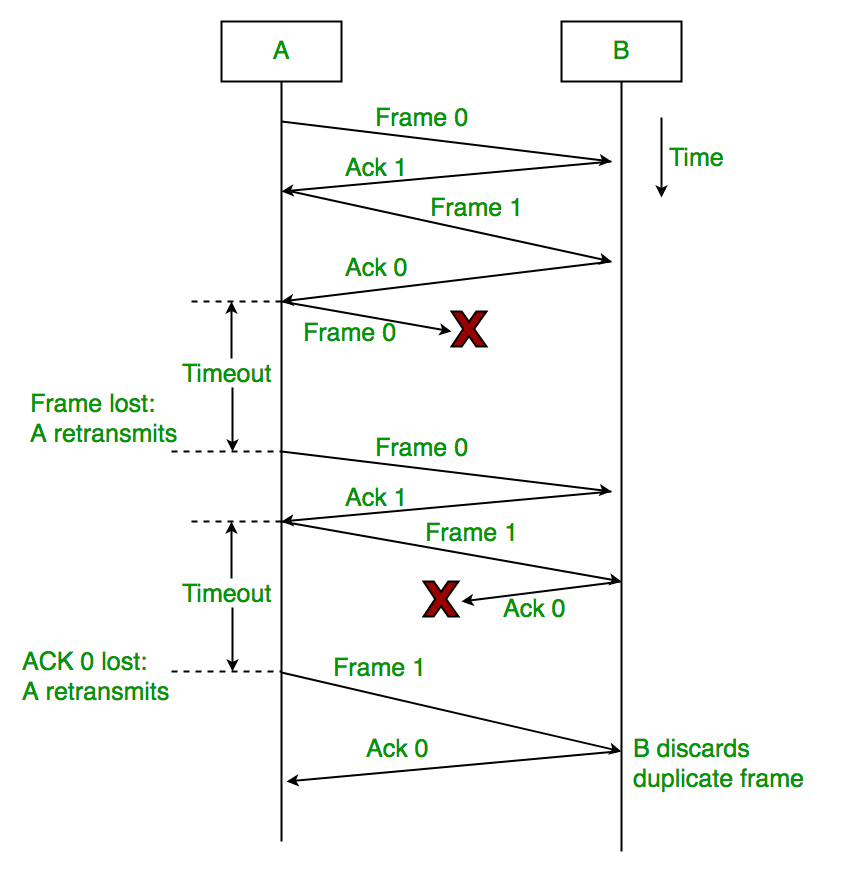
source:geeksforgeeks
Pros: Simple and effective.
Cons: Low efficiency for high-latency networks.
Go-Back-N ARQ:
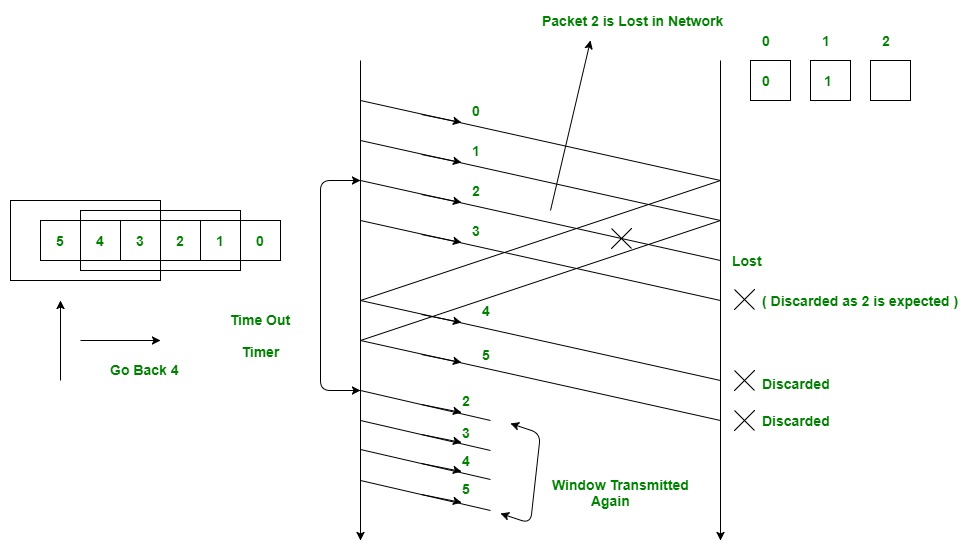
source:geeksfrogeeks
The sender transmits multiple frames and keeps track of the sequence numbers. If an error is detected, it retransmits from the erroneous frame.
Pros: Better efficiency than Stop-and-Wait.
Cons: Resends entire window upon error detection.
Selective Repeat ARQ:

source:geeksforgeeks
Similar to Go-Back-N but only retransmits the erroneous frame.
Pros: High efficiency.
Cons: Requires more complex hardware.
Working Process:
Sender transmits data frames to the receiver.
Receiver checks for errors using CRC or other error-detection methods.
If the data is error-free, an acknowledgment (ACK) is sent.
If errors are detected, a negative acknowledgment (NACK) is sent, prompting retransmission.
Applications:
Data Communication: Used in protocols like TCP/IP.
Wireless Networks: Ensures reliable data transmission in mobile networks.
Q.4 OR (a) Enlist various error detection techniques and explain any one. (3 Marks)
Enlisted Techniques:
Parity Check.
Cyclic Redundancy Check (CRC).
Checksum.
Hamming Code.
Explanation of CRC:
Cyclic Redundancy Check (CRC) uses polynomial division to detect errors in transmitted data. The sender appends a CRC code to the data, and the receiver recalculates the CRC. If the recalculated CRC doesn’t match, errors are detected.
Use:
Widely used in network protocols like Ethernet.
Q.4 OR (b) Describe Multiple Access with Collision Avoidance. (4 Marks)
Definition:
Multiple Access with Collision Avoidance (MACA) is a protocol used in wireless communication to minimize collisions by coordinating access to the shared channel.
Working Process:
Request to Send (RTS): The sender transmits an RTS frame to the receiver.
Clear to Send (CTS): The receiver responds with a CTS frame, granting permission.
Data Transmission: The sender transmits data after receiving CTS.
Acknowledgment (ACK): The receiver sends an ACK after successful reception.
Advantages:
Reduces collisions in a shared medium.
Improves network efficiency.
Applications:
Used in IEEE 802.11 wireless networks (Wi-Fi).
Q.4 OR (c) Describe Wireless Application Protocol (WAP). (7 Marks)
Definition:
Wireless Application Protocol (WAP) is a standard framework that enables mobile devices to access internet services and applications over wireless networks.
Key Components of WAP:
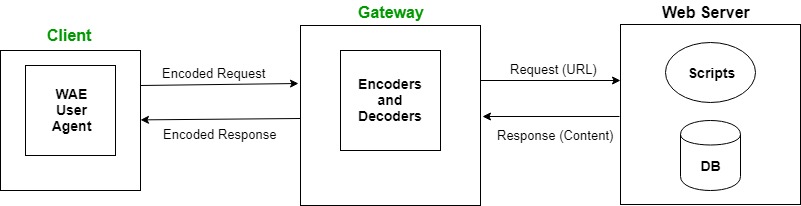
WAP Gateway: Translates WAP requests into HTTP requests and vice versa.
WAP Protocol Stack: Consists of layers like Wireless Session Protocol (WSP) and Wireless Transaction Protocol (WTP).
WAP Browser: A lightweight browser on mobile devices to access WAP content.
WAP Protocol Stack:
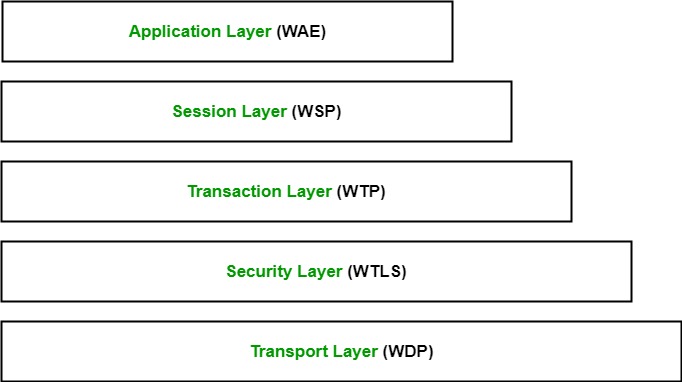
Application Layer: Manages user interaction and content display.
Session Layer (WSP): Provides session management.
Transaction Layer (WTP): Ensures reliable communication.
Security Layer (WTLS): Provides encryption and authentication.
Transport Layer (WDP): Manages data transmission over various bearer networks.
Applications:
Mobile banking.
Email and instant messaging.
Online ticket booking.
Limitations:
Limited multimedia support compared to modern standards.
High dependency on network speed.
Q.5 (a) Write use of Manifest file. (3 Marks)
Definition:
In Android, the Manifest file (AndroidManifest.xml) is a crucial configuration file that provides essential information about the app to the Android system.
Uses of the Manifest File:
Declares App Components: It defines key components like activities, services, broadcast receivers, and content providers.
Permissions: Specifies the permissions the app requires to access system resources (e.g., camera, location).
App Features: Declares app requirements such as hardware features (e.g., camera, GPS) and SDK versions.
Intents and Filters: Associates app components with specific intents and defines intent filters to determine how components respond to certain actions.
Q.5(b) Enlist Various Android Layouts. Describe any one.. (4 Marks)
Definition:
An Android layout defines the visual structure of a user interface for an application, specifying the arrangement of UI components.
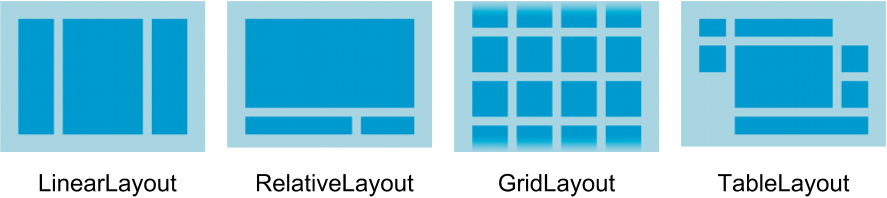
Types of Android Layouts:
Linear Layout:
Aligns child views in a single direction (horizontal or vertical).
Example: A vertical list of text boxes.
Relative Layout:
Positions elements relative to each other or parent.
Example: Placing a button below a text field.
Constraint Layout:
Allows complex layouts with constraints to parent or sibling elements.
Example: A responsive screen design.
Frame Layout:
Stacks child views on top of each other.
Example: Overlaying a loading icon on an image.
Table Layout:
Arranges elements in rows and columns.
Example: A form with labels and text fields.
Description of LinearLayout:
LinearLayout arranges its child elements in a single horizontal or vertical direction.
Attributes:
orientation: Defines whether the child elements are laid out horizontally or vertically.
layout_width and layout_height: Determines the size of the layout.
code:
Example Use Case:
Typically used when you want to align elements such as buttons or text fields in a single row or column.
Advantages:
Provides flexible UI design options.
Supports responsive designs for different screen sizes.
Conclusion:
Choosing the right layout depends on the application's complexity and user experience goals.
Q.5 (c) Draw and Explain Bluetooth Protocol Architecture. (7 Marks)
Definition:
Bluetooth protocol architecture defines layers and protocols used to manage Bluetooth communication effectively.
Architecture Layers:
Radio Layer: Handles physical transmission using radio frequencies.
Baseband Layer: Manages connection establishment and packet formatting.
Link Manager Protocol (LMP): Ensures security and connection control.
Host Controller Interface (HCI): Provides communication between hardware and software.
Logical Link Control and Adaptation Protocol (L2CAP): Handles multiplexing and segmentation.
Application Layer: Runs user-level applications like file transfer and audio streaming.
Diagram:  source:geeksforgeeks
source:geeksforgeeks
Applications:
Wireless peripherals like headphones and keyboards.
File sharing between devices.
Limitations:
Limited range of around 10 meters.
Potential interference from other devices.
Q.5 OR (a) Differentiate Wi-Fi and Wi-Max. (3 Marks)
| Feature | Wi-Fi | Wi-Max |
|---|---|---|
| Definition | Wireless technology for short-range networking (typically up to 100 meters). | Broadband wireless technology designed for long-range networking (up to 50 km). |
| Frequency Band | Operates in 2.4 GHz and 5 GHz bands. | Operates in 2.3 GHz, 2.5 GHz, and 3.5 GHz bands. |
| Speed | Data speeds up to 54 Mbps (Wi-Fi 802.11g) and higher with 802.11n/ac/ax. | Provides speeds from 1 Mbps to 75 Mbps, depending on the range and technology. |
| Range | Typically within 100 meters, suitable for home and small office environments. | Designed for large coverage areas, up to 50 km. Suitable for metropolitan areas. |
| Applications | Used for internet access, LANs, and hotspots. | Primarily used for broadband access in large geographic areas (e.g., citywide internet access). |
Q.5 OR (b) Describe Piconet and Scatternet. (4 Marks)
Definition:
Piconet: A small Bluetooth network consisting of one master and up to seven active slaves.
Scatternet: A collection of interconnected piconets where devices participate in multiple piconets as masters or slaves.
Features:
Piconet:
Simple topology.
Short-range communication.
Scatternet:
Complex but supports more devices.
Allows multiple connections.
Uses:
Piconet: Headphones, keyboards, and other peripherals.
Scatternet: Multi-device setups like smart homes.
Q.5 OR (c) Describe Android Architecture. (7 Marks)
Definition:
The Android Application Framework provides a set of APIs for building applications on the Android platform. It is the foundation for creating and managing the core functionality of Android apps.
Android Architecture.

source:javatpoint
1) Linux kernel:
It is the heart of Android architecture that exists at the root of Android architecture. Linux kernel is responsible for device drivers, power management, memory management, device management, and resource access.
2) Native Libraries:
On top of the Linux kernel, there are Native libraries such as WebKit, OpenGL, FreeType, SQLite, Media, C runtime library (libc), etc.
- The WebKit library is responsible for browser support.
- SQLite is for database management.
- FreeType is used for font support.
- Media handles playing and recording audio and video formats.
3) Android Runtime:
In the Android runtime, there are core libraries and DVM (Dalvik Virtual Machine) that are responsible for running Android applications. DVM is similar to JVM but optimized for mobile devices. It consumes less memory and provides fast performance.
4) Android Framework:
On top of Native libraries and Android runtime, there is the Android framework. The Android framework includes Android APIs such as UI (User Interface), telephony, resources, locations, content providers (data), and package managers. It provides many classes and interfaces for Android application development.
5) Applications:
On top of the Android framework, there are applications. All applications such as home, contact, settings, games, and browsers are built using the Android framework that utilizes Android runtime and libraries. Android runtime and native libraries depend on the Linux kernel.
Key Features:
- Provides modular architecture for app development.
- Allows handling user interface, background processes, and data management efficiently.
- Enables component-based development, where each feature of an app is managed by different components.
Advantages:
- Reusable components that save development time.
- Seamless integration of UI and non-UI functionalities.
- Facilitates multitasking and background operations in Android apps.


0 Comments